Cybersecurity is a game of foresight. It’s a chessboard on which attackers and defenders are constantly looking for checkmate.
Hackers launch a new ransomware attack every 14 seconds. They’re increasingly more capable and sophisticated. Learning how they plan attacks, what techniques they use, and who they’re targeting, can make you so much better prepared. You’ll save the cost and headache of a cyber assault too. This is especially important considering that the cost of ransomware attacks in the U.S. alone surpassed $7.5 billion in 2019.
But investigating malware threats is tedious. Hundreds of new articles and tweets need to be reviewed and triaged every day. Finding critical threats in that sea of information is time-consuming and overwhelming.
We want to help you streamline your tactical and operational open-source intelligence, so that you can better protect your environment.
That’s why we’ve taught Leo, your AI research assistant, to recognize malware threats. You can ask him to read your security feeds and prioritize what’s relevant to you, your sector, and your environment.
Let’s imagine that you work in a threat intelligence team and are responsible for researching and analyzing the threat landscape. You’re particularly interested in evolving malware threats (including ransomware and malvertisement).
Cut through the noise
You can train Leo to read your Security News feed and prioritize articles related to malware.
Leo continuously reads the thousands of articles published in those feeds. It’s an efficient way to cut through the noise and keep up with the evolving malware landscape without the overwhelm.
You’re in control
Leo has been trained to understand broad topics like malware, as well as hundreds of specific malware types like malvertisement, ransomware, adware, bots, rootkits, spyware, etc.
Asking Leo to prioritize malware in your Security News feed is as simple as creating a new Topic priority and selecting ‘malware’ as the topic.
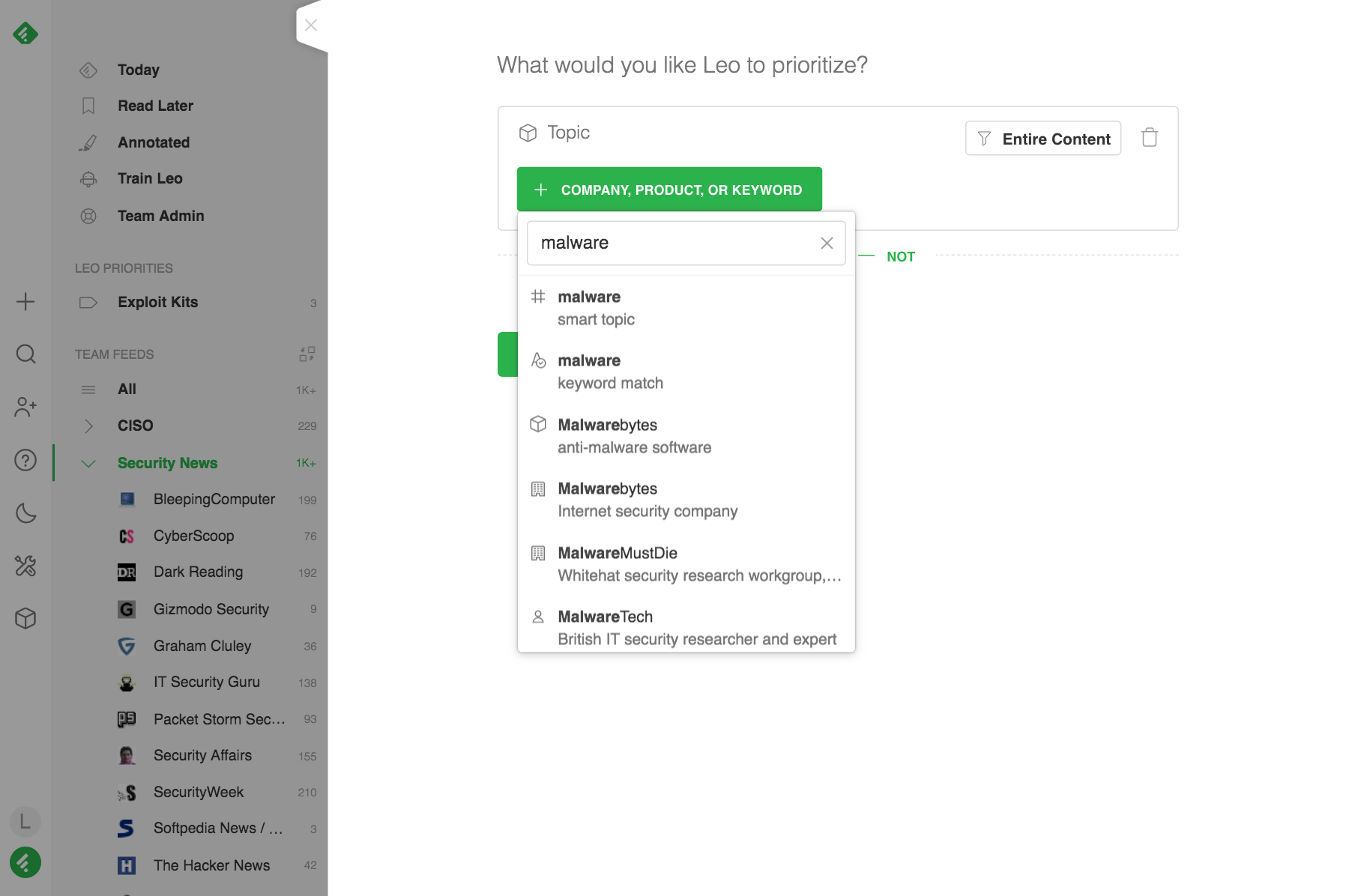
You can combine topics with +AND and +OR and create even more targeted priorities for Leo. For example, use +AND to focus on malware related to Android or top companies in your sector.

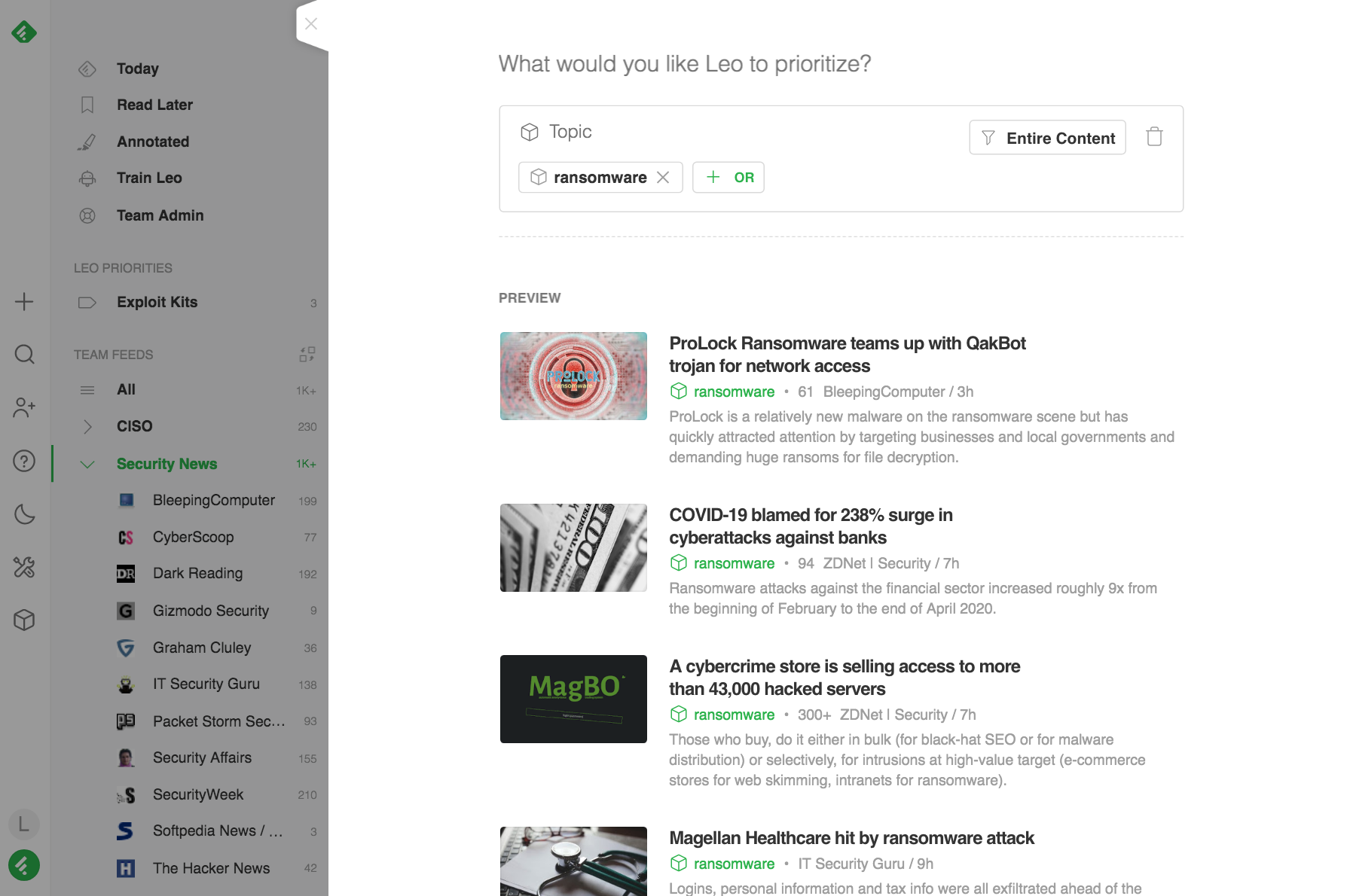
You can also ask Leo to look for a specific type of malware like malvertisement or ransomware.
Continuously learning and getting smarter
Leo is smart. He continuously learns from your feedback. When Leo is wrong, you can use the ‘Less Like This’ down arrow button to let him know that an article he’s prioritized isn’t about malware.
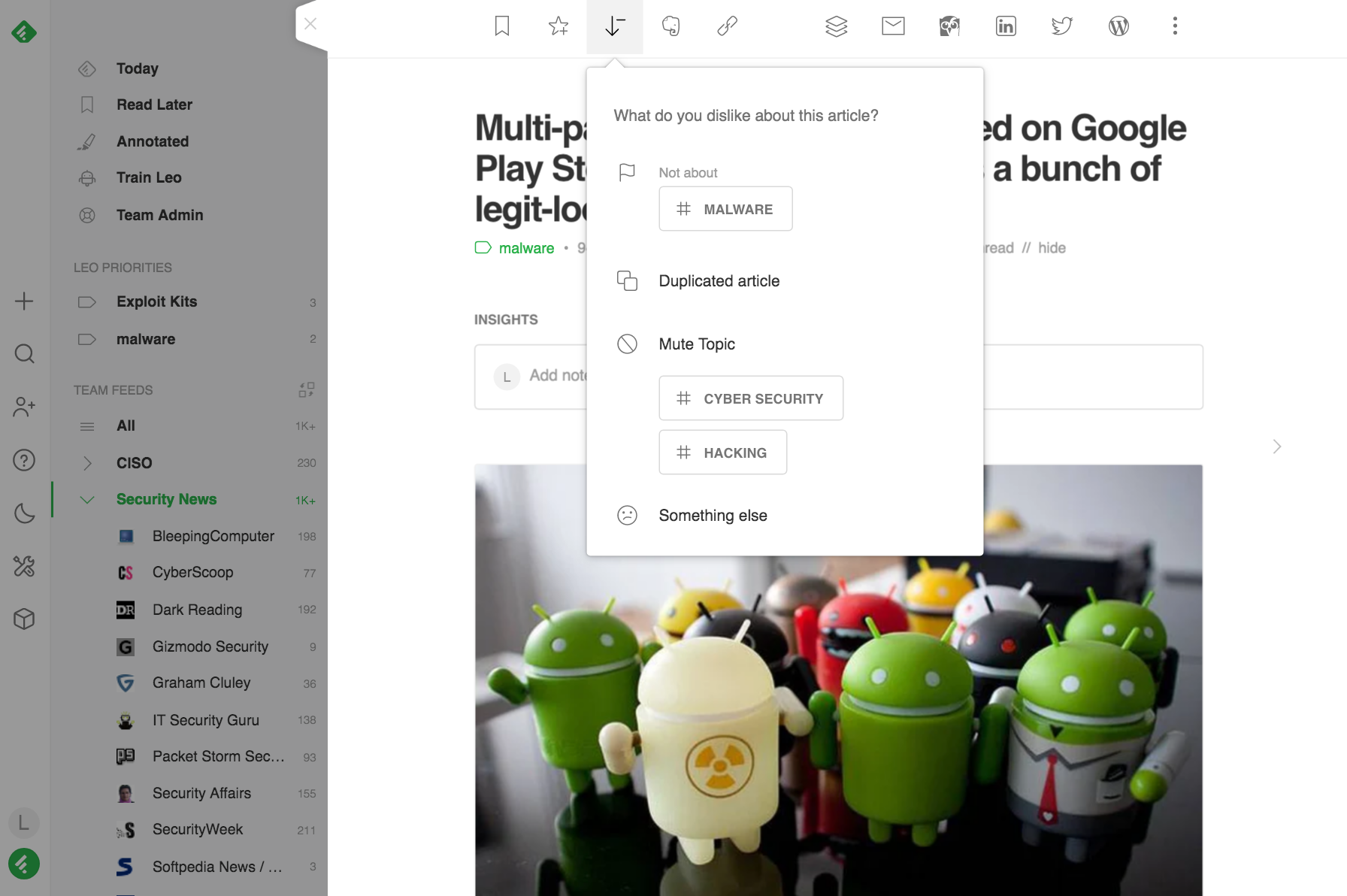
Break down silos
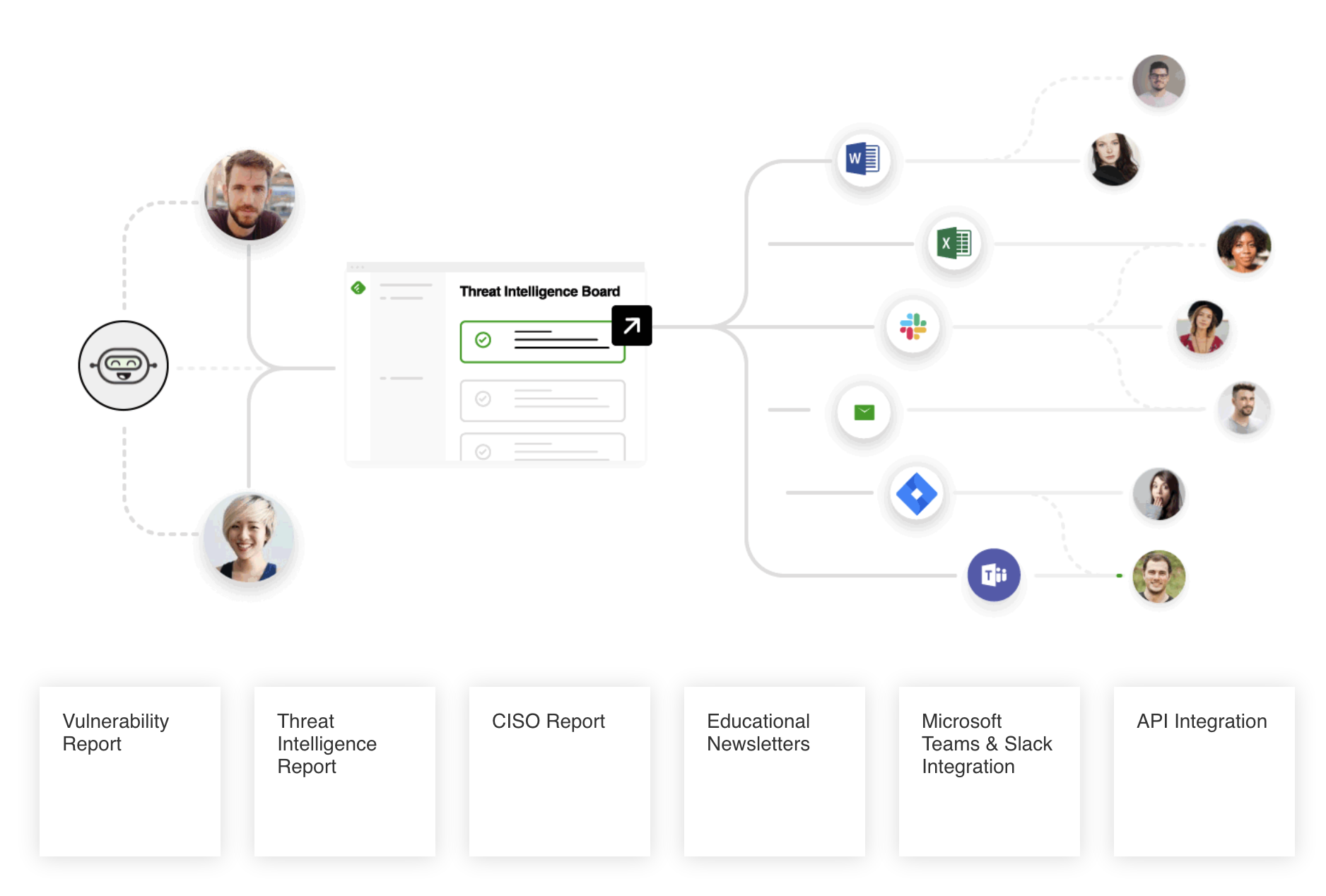
Bring your research team into the picture. They can create a Threat Intel Report Board and save the most critical insights they discover in their Feedly. Then everyone with the same Board can leave notes and highlight the biggest threats.
We’ve seen teams create tactical and operational Boards. For instance, a Vulnerability Report can be built up with information for those that deal with security procedures, while strategic CISO Newsletters can keep management up to speed about malware and your planned response.
Articles bookmarked in a Board can be shared with the rest of the team via daily newsletters, Slack and Microsoft Teams notifications, or pushed to other apps using the Feedly Cybersecurity API.
Streamline your open-source intelligence
We’re excited to see how your security team will declutter your feeds and dig deeper into the critical threats that matter to you. Sign up today and discover Feedly for Cybersecurity.