The analyst team at this company needed better tools to help leverage their time and attention and stop doing manual research. Joe’s team had been using Feedly to aggregate information for years. But when his boss, Oliver, Cyber Security Manager, found out that Feedly’s cybersecurity-specific plan could use AI to flag cyber attacks, threats, and vulnerabilities, they knew they had to try it.
Organizing their security sources into focused Feeds
Oliver created Feeds around three main focus areas: renewable energy sources + cybersecurity, critical vulnerabilities, and supply chain threats.
The team selected sources of information they trusted to track cybersecurity news. Not all articles from their trusted sources concern the energy sector. To filter out cybersecurity news unrelated to the energy sector, they configured Leo, Feedly’s AI research assistant, to flag articles about the specific areas they care about.
“Before using Leo, we had very generic Feeds. We were just looking for energy and cybersecurity news in our region. But over time, I’ve been able to nuance our requirements over supply chain attacks, like Solar Winds.”
Tracking ransomware in the energy space
For example, the analyst team has always tracked news at the intersection of cybersecurity and the energy sector. But once they started using Feedly for Cybersecurity, they created a Leo Priority to flag articles that cover ransomware in the energy industry.
Tracking supply chain attacks
“We were concerned about the supply chain risk for our company,” says Joe. “We talked to our internal procurement team to really understand our top 30 providers, with whom we spend millions of dollars.”
To track supply chain risks, the team selected the exact vendors they work with and created a personalized stream of intelligence to track risks coming from their supply chain. “We were able to turn the list of our top partners into a Leo Priority and ask him to flag cyber attacks targeting those partners,” explains Joe.
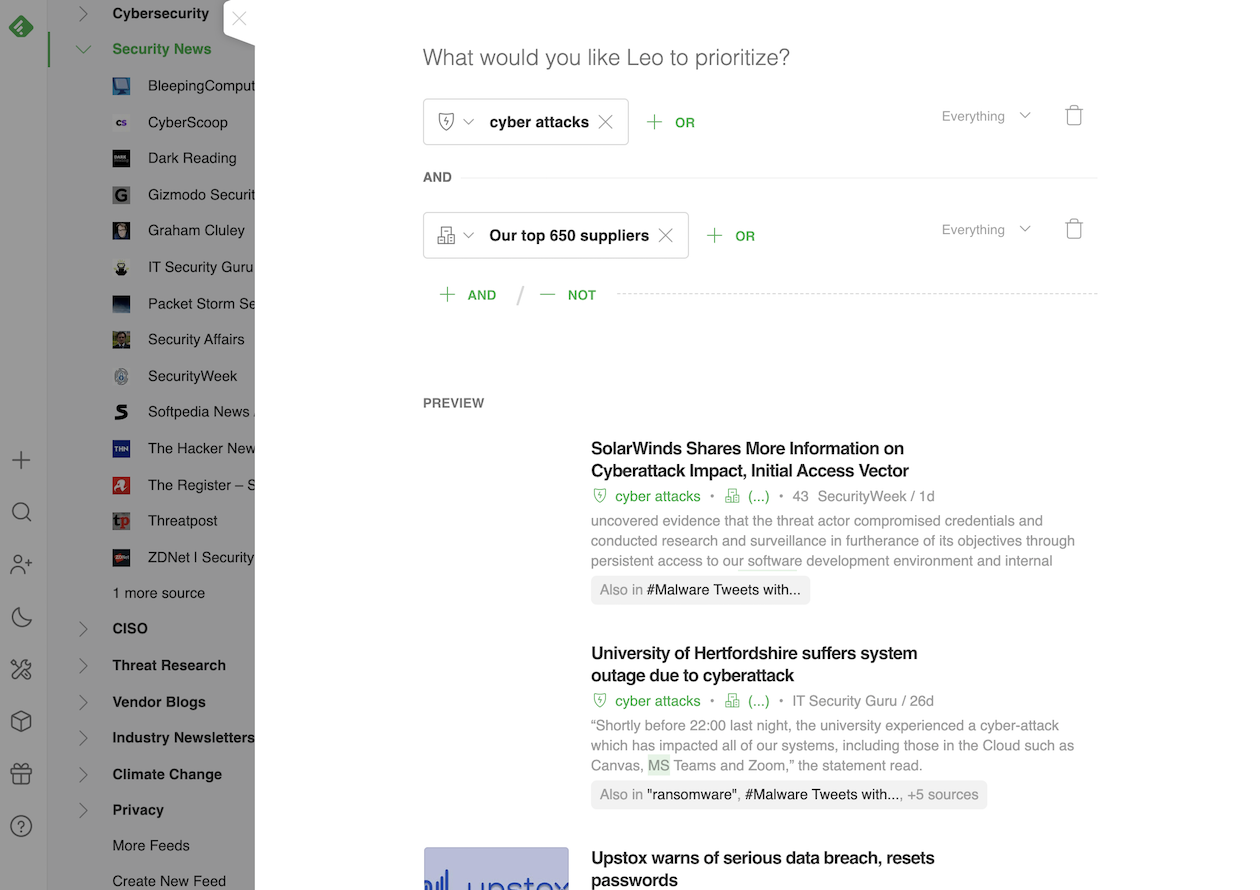
With a Priority in place, Leo flags articles about data breaches related to any of the company’s suppliers, so they’ll know when one of the companies in their supply chain is breached or attacked. Leo recognizes most of these names as companies, so he can differentiate if an attack is about Amazon (company) vs. Amazon (the river), for example.
Pushing articles to Slack to share with the local intelligence community
Beyond their internal intelligence team, Joe and Oliver share information across several platforms with peer organizations cybersecurity teams around the globe.
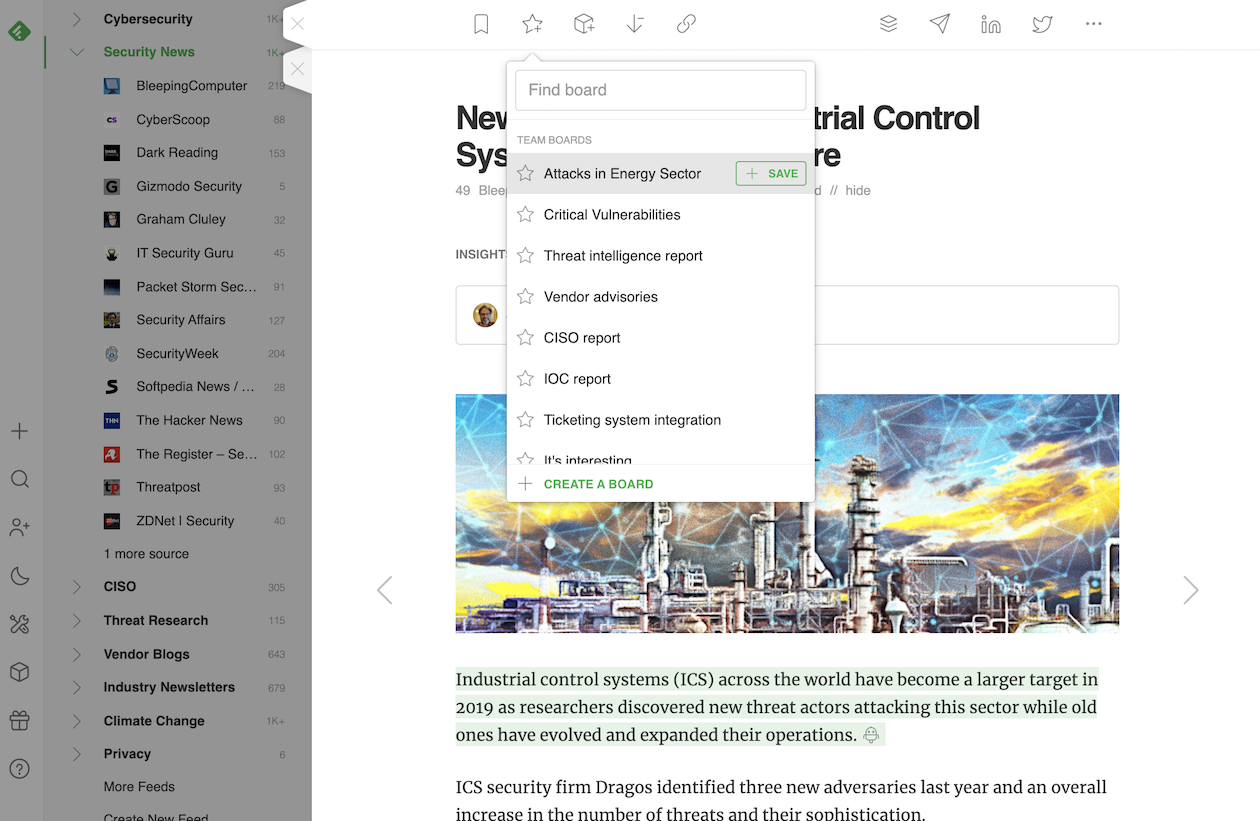
Joe and Oliver add critical articles to a specific Feedly Board. They’ve connected the Board to the collaboration platforms, so when Joe or his teammates add articles to the Board, their security community will automatically see critical updates.